“A ship is safe in harbor, but that’s not what ships are built for.”
—John A. Shedd
Cyber refers to the digital world and all things related to technology and the internet. This includes online communication, computers, networks, and the security of these systems from unauthorized access and harm. In short, cyber refers to the virtual world and ensuring its safety.
So, cybersecurity is the practice of protecting computer systems, networks, and internet-connected devices from digital attacks, theft, and damage. This involves implementing various technologies, processes, and practices to secure sensitive information and prevent unauthorized access, hacking, and other cyber threats. The goal of cybersecurity is to keep the internet and connected devices safe and secure for individuals, businesses, and governments.
Information security and cybersecurity are closely related but slightly different concepts. Information security refers to the protection of information and data from unauthorized access, use, disclosure, disruption, modification, or destruction. This encompasses a wide range of practices and technologies, including access control, encryption, firewalls, and backup and recovery systems.
Information Security = Cyber + Physical
In short, information security is a broad term that encompasses all aspects of protecting information, while cybersecurity specifically focuses on the protection of digital systems and networks.
To make information security solutions precisely effective, clients focus on use cases. In the context of cybersecurity, a use case is a specific scenario or situation that describes how a security event or incident should be detected, investigated, and/or responded to by an organization’s security operations team. A use case typically includes a set of rules, criteria, or thresholds that define what constitutes an abnormal or suspicious activity that requires further investigation or response.
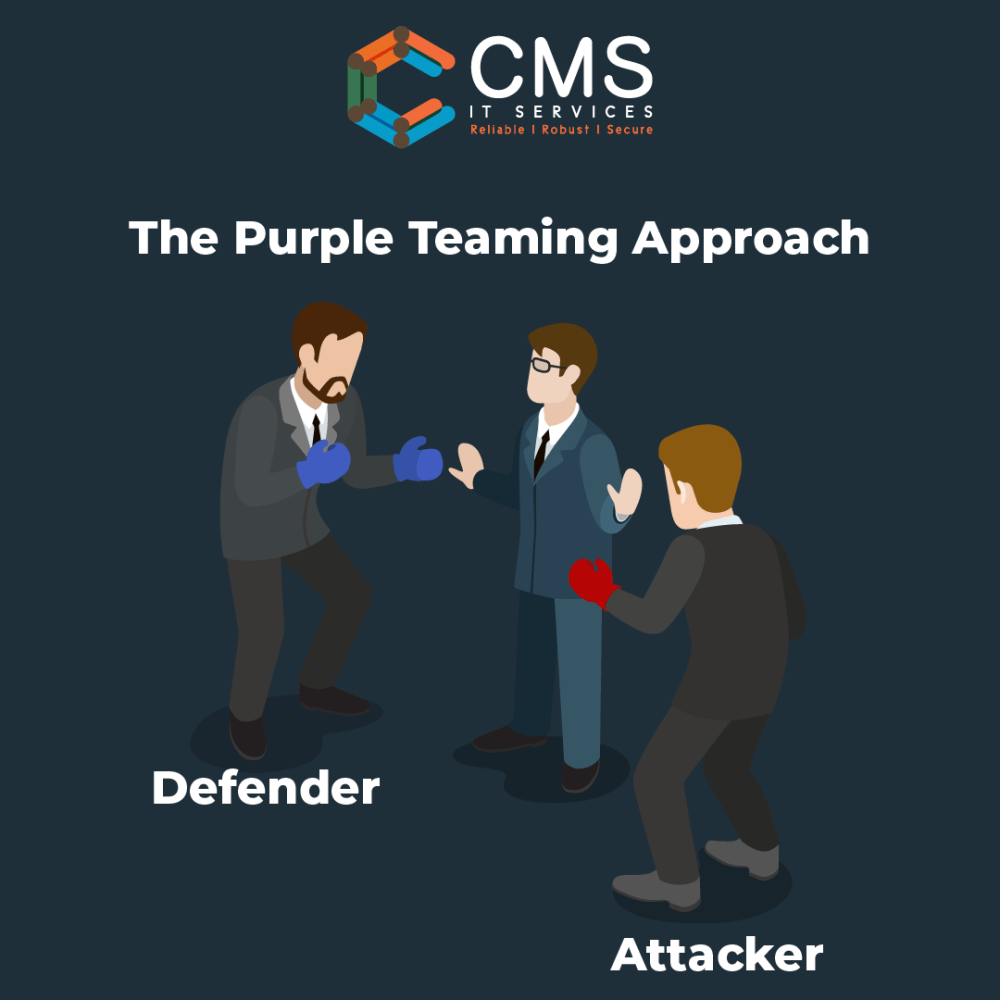
Purple is commonly used in information security- purple from mixing red for offense and blue for defense. Purple Teaming is a collaborative process that combines the expertise and knowledge of both the “blue team” (defenders) and the “red team” (attackers) to improve an organization’s cybersecurity defenses. The objective of Purple Teaming is to identify and close gaps in an organization’s security posture, as well as to improve the effectiveness and efficiency of the overall security strategy. In a Purple Team engagement, the blue team provides the red team with access to its systems, tools, and processes, and then actively works with them to identify vulnerabilities, test defenses, and develop mitigation strategies. Through this collaboration, the blue team gains a better understanding of the organization’s vulnerabilities, and the red team learns how to improve its attack methodologies. The Purple Teaming approach helps organizations to prepare better for real-world attacks and to improve their security posture over time continuously.
If you have any thoughts or questions about your organisation’s security postures or initiatives, feel free to write to info@cmsitservices.com.