As we head into 2021, enterprises are looking to shed the limitations of a traditional enterprise and move to a model that is flexible, accessible, and yet scalable. Irrespective of the kind of business, digital or brick and mortar, enterprises across the industry spectrum are putting together plans to transform their businesses to take advantage of cloud-based capabilities to make them more and more agile and responsive to addresses future risks. At CMS IT we believe this is the new normal.
With cloud adoption increasing at an exponential rate, cybercriminals are not far behind. Cybercrimes cost an unprecedented $6 trillion in 2020! And the most common root cause is unmanaged change. Cybersecurity in the face of change brings forth a few challenges –
With its core focus on change adaptability, Defensible Cybersecurity is uniquely positioned to arm its clients with the ability to protect against, detect and respond to cyber-attacks that can disrupt Cloud Transformation. Defensible Cybersecurity is a standards-based end-to-end cybersecurity program that is a holistic approach to address cybersecurity challenges, aligned to the context of business, addressing systemic issues, challenges, and stakeholder requirements, designed to handle constant change while continuously improving operational controls, designed to address cybersecurity risks for both traditional & digital businesses and their supply chains.
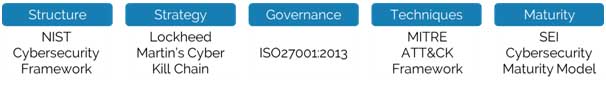
Defensible Cybersecurity addresses 3 main challenges that enterprises face when transforming their businesses using Cloud Solutions.
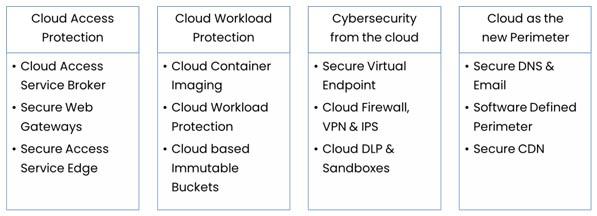
Information protection and its design requires careful consideration and cloud security solutions for protection falls into the following categories –
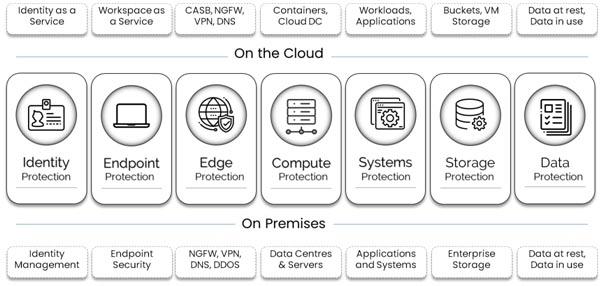
CMS IT Services realizes that selecting the right solution for your Cloud Transformation initiative is key to your success when handling cyber disruptions and that is exactly why Defensible Cybersecurity suggests that you review your cybersecurity controls using 7 distinguishable points of control.
The most essential tool to address change is to have a formal program that can monitor and detect the change and act instantly to make necessary corrections. CMS IT recommends considering a ‘Detect’ solution, as soon solutions and mechanisms to Protect are established.
Nearly all successful attacks on cloud services are the result of customer misconfiguration, mismanagement, and mistakes.” — Neil MacDonald, Gartner analyst
On a constantly changing cybersecurity landscape, monitoring and detection of the applications, their underlying infrastructure, service dependencies and Cloud Compliance are absolutely critical to be ahead of the cyber attackers. CMS IT recommends 5 key capabilities in every detection program.
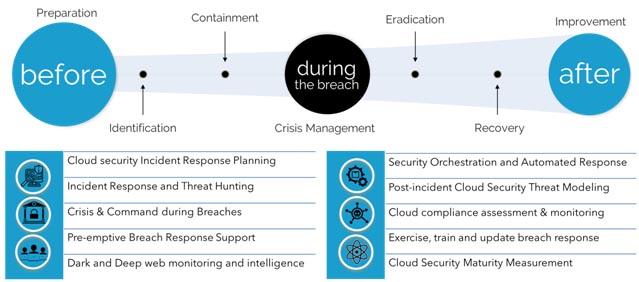
While Detect solutions like XDR or eXtended Detection and Response include capabilities to respond to the Indicators of Attack (IoA) and the Indicators of Compromise (IoC), any cybersecurity attack needs a more formal coordinated response capability.
Most standards and regulations insist the Cybersecurity Response capabilities must be considered before, during, and after a cybersecurity attack. CMS IT Services provides services to prepare for, respond to, withstand and recover from a cyber-attack, use the Integrated Cybersecurity Command Center to build pre-emptive response, command, and control and threat hunting as may be required to address threats.
Aws
Founded in 1975, Microsoft (Nasdaq “MSFT”) is the worldwide leader in software, services, devices and solutions that help people and businesses realize their full potential.Microsoft builds robust IT offerings to enable users to develop and share ideas, find solutions, and stay connected to what’s most important. They are motivated and inspired that 95 percent of the enterprise workforce in India uses Microsoft platforms to create, contribute, and innovate.
CMS IT SERVICES is a CSP for Microsoft in many key markets and is redefining strategic imperatives for business through these relations. CMS IT SERVICES having Microsoft as alliance, help customers achieve optimized levels of business performance, through assessment, advisory services, and application integration plus migration services. CMS IT SERVICES collaborate with Microsoft to deliver distinctive capabilities, offering clients high performance Infrastructure solutions regardless of their business challenges.
As a leading IT services provider we focus on AI-led Managed Services and Digital Transformation. We are committed to help you change the way you organize your IT operations, bring meaningful and actionable insights to your service improvements through advanced ML. We want to enhance experience of your users and reduce your resource utilization. For delivering these services, we have partnered with GAVS’ AIOps platform, Zero Incident Framework TM (ZIF). It enables proactive detection and remediation of incidents and increases uptime, helping organizations drive towards a Zero Incident Enterprise. It is can be an on-premise or a SaaS solution based on the usecase. It enables IT to deliver high performing systems with end to end visibility that helps manage and optimize resources and assets, and drives value for businesses. The platform also prevents data disasters and enhances business services continuity.
Ready to customize your business’s cybersecurity approach?
We’re here to help.