CSOC SI- What is it and what are the problems it solves?
All things considered, 2021 and beyond, cybersecurity modernisation will be a top priority. Bolstering the current security posture by closing the gap attack surfaces with or without the Cloud First journey, diligently holding compliance, and integrating cybersecurity into business will be a complex and continual effort.
As the threatscape trends and the attack tactics, techniques, procedures continue to evolve, defensible cybersecurity operations centre (CSOC) solution design, architecture assessment, technology optimization, product supply and implementation, systems integration, organisation-wide policies and controls orchestration and adoption, cross-technology training, go-live critical assistance and 24×7 monitoring, management, and governance, will require skilled enterprise security architects, alacritous cyber-responders and self-driven threat-hunters, and level-headed technologists and program heads.
To ensure optimal protection while lowering investments in implementing, integrating, and maintaining effective enterprise-wide security, CMS IT can help you maximize the use of your existing and new technologies.
We deliver 24/7 tailor-made and compliant CSOC systems’ planning, supply, integration, operations, and management, that is,
| RAMSISC-Reliable | Available | Maintainable | Safe | Interoperable | Scalable |
Why Choose CMS IT?
| Technology and Governance Yantra |
Process and Collaboration Tantra |
People and Intelligence Mantra |
| Customer-First services model with business-aware technology solutions and innovative transparent pricing models | Defensibility of services structure and strategy aligned to NIST Cybersecurity Framework and Lockheed Martin’s Cyber Kill Chain respectively | Expertise and talent pool of 5000+ trained and certified professionals with an unmatched level of technical competencies across technologies |
| Output-based pricing models with a flexible asset refresh and financing strategy | Design guidance linked to OWASP, Cloud Security Alliance | Vendor Agnostic Partnerships with 40+ OEMs |
| Platform-based standardization with X-as-a-Service offerings on the hybrid option of services delivery | Techniques integrated with MITRE ATT&CK and R3SPOND enterprise | Swift skillset mapping, resources onboarding, resource rebadging (as applicable) |
| Accurate Service Integration and Management(SIAM) in design, implementation, and integration of multiple tools from multiple vendors | Controls based on CIS 20 version 7 Controls and COBIT | Intelligent Resource Optimization with AI/ML-based tools, automation, and smart monitoring |
| 27-point demonstrated SIMSS CITRA Model of System Integration with accelerator best practices and automation | Governance built on ISO 27001 family of standards | Policy-driven Automation and Optimization |
| Unmatched focus on quality delivery with professional Project Management and Risk Management methodologies | Secure by design compliance aligned to RBI/IRDAI/MEITY/ SEBI/NCIIPC/GoI/GDPR guidelines | Dedicated 24×7 Centres of Excellence and Innovation |
| Yantra in classical Sanskrit means apparatus or contrivance- from the root word, yam, meaning “to sustain the essence of an object/concept.” | Tantra in Sanskrit means woven together- the physical with the spiritual | Mantra refers to a statement or a principle that people repeat very often because they think it is true |
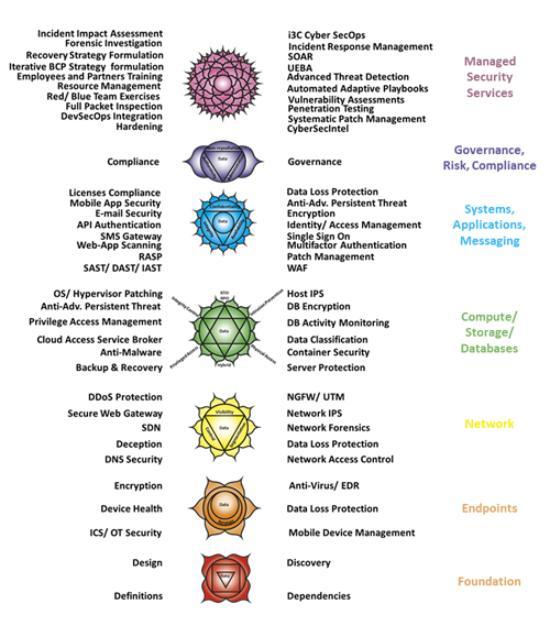
CSOC SI- Components
Chakras are the energy centres of the body and relate to specific spiritual, emotional, psychological and physical aspects of our being. Blockage or malfunction of the chakras can lead to physical, psychological, and emotional disorders. The conscious awareness and the balancing of these energy centres on the other hand is believed to lead to well-being and good health. With iterative practice, one can stimulate and balance the chakras or energies in the body.
| Organisation’s security is the body | All chakras here are activated at full maturity | CMS IT’s CSOC SI encompasses all chakras |
Trend Micro Incorporated, a global leader in cybersecurity solutions, helps to make the world safe for exchanging digital information. Our Innovative solutions for consumers, businesses, and governments provide layered security for data centres, cloud environments, networks, and endpoints.
All our products work together to seamlessly share threat intelligence and provide a connected threat defense with centralized visibility and control, enabling better, faster protection.
With over 5,000 employees in over 50 countries and the world’s most advanced global threat intelligence, Trend Micro enables organizations to secure their journey to the cloud. For more information, visit www.trendmicro.com.
CMS IT work closely with Trend Micro in sales engagement and implementation process to take their technology to CMS IT customer base and beyond. We leverage our experience to understand how customers want to plug in best security solution to their information security requirement.
As a managed security service partner, CMS IT has a pool of experts to draw on their hands-on experience and insights in Trend Micro’s security portfolio.
Cisco is the worldwide leader in IT and networking. It helps companies of all sizes transform how people connect, communicate, and collaborate. Their product comprises of the following categories: Switches, Routers, Wireless, Network Management Interfaces and Modules, Optical Networking, Access Points, Outdoor and Industrial Access Points, Next-Generation Firewalls, Advanced Malware Protection, VPN Security Clients, Email, and Web Security.
We are a System Integrator and service provider of Cisco with PAN India presence. We have a large Cisco certified resource pool.
Ilantus has a unique product range in Identity management and Identity Governance and Administration. It is ahead of the curve in terms of technology. It is a SAAS product which is breaking all price barriers.
With CMS IT services having huge experience in EUC and cyber security, It is very easy to jump start your Identity and Access management with minimal effort and cost.
CyberArk is the global leader in privileged access security, a critical layer of IT security to protect data, infrastructure and assets across the enterprise, in the cloud and throughout the DevOps pipeline.
CyberArk delivers the industry’s most complete solution to reduce the risk created by privileged credentials and secrets. It is trusted by the world’s leading organizations, including more than 50 percent of the Fortune 500, to protect against external attackers and malicious insiders.
With CyberArk we secure enterprises against cyber-attacks that take cover behind insider privileges to attack critical enterprise assets. Together we deliver a new category of targeted security solutions that help leaders stop reacting to cyber threats and get ahead of them, preventing attack escalation before irreparable business harm is done.
Smokescreen brings military deception tactics to the digital battlefield. Their solutions protect some of the most highly targeted organisations globally, including leading financial institutions, critical infrastructure, and Fortune 500 companies.
They have the industry’s largest library of deception techniques. No one else covers pre-attack foot-printing, spear-phishing, web application attacks, social-engineering, data theft, Active Directory attacks, and more.
Our customers get far more than just the product — they get the Smokescreen play-book and our support. With tools and expertise, we guarantee we’ll reshape how you approach cybersecurity both strategically and tactically.
Fortinet provides top-rated network and content security, as well as secure access products that share intelligence and work together to form a cooperative fabric.
The unique Security Fabric combines Security Processors, an intuitive operating system, and applied threat intelligence to give you proven security, exceptional performance, and better visibility and control–while providing easier administration. The flagship product, enterprise firewall platform, FortiGate, is available in a wide range of sizes and form factors to fit any environment.
Complementary products that we resell along with FortiGate to enable a simplified, end-to-end security infrastructure cover:
Network Security – Protect the entire attack surface from headquarters to branch offices with advanced security.
Multi-Cloud Security – Complete visibility and control across the cloud that enables secure applications and connectivity.
Secure Access – Deliver secure application, device access, and management without compromising performance and speed.
Security Operations – Implement advanced threat intelligence to detect, prevent, and respond sophisticated malware and improve security awareness.
Network Operations – Leverage a smart security strategy that prioritizes automation-driven network operations that spots and prevents network breaches.
Endpoint and Device Protection – Proactive protection, visibility, and control for all endpoints and devices across the network.
Application Security – Protect critical business web applications with an integrated set of products to thwart advanced threats.
MDR – Manged Detection and Response
MDR – Manged Detection and Response
IAM – Identity and Access Management
IAM – Identity and Access Management
Cybersecurity GRC Advisory
Cybersecurity GRC Advisory
SATE – Security at the Edge
SATE – Security at the Edge
Cloud Security
Cloud Security
Ready to build a cyber resilient organization?
We’re here to help.
Error: Contact form not found.












