The Security Operations Centre (SOC) is an essential part of an organization’s cybersecurity strategy. As cyber threats continue to evolve, the SOC must also evolve to keep pace with these changes.
Here are ten characteristics of the next generation SOC:

- Real-time threat detection: The next generation SOC must be able to detect threats in real-time to respond quickly to cyber incidents.
- Automation and orchestration: The SOC should leverage automation and orchestration to streamline its operations, allowing analysts to focus on high-level tasks.
- Integration with other security technologies: The next generation SOC should integrate with other security technologies such as endpoint protection, firewalls, and threat intelligence platforms to provide a more comprehensive defense.
- Artificial Intelligence and Machine Learning: AI and ML can help automate routine tasks, identify patterns, and improve the accuracy and speed of threat detection.
- Cloud-native: The next generation SOC should be cloud-native, allowing for better scalability and flexibility.
- Integrated Incident Response: The SOC should have an integrated incident response plan, enabling analysts to respond to security incidents quickly and effectively.
- DevSecOps: The next generation SOC should embrace DevSecOps practices, ensuring that security is integrated throughout the development process.
- Proactive threat hunting: The SOC should proactively search for threats, rather than just responding to alerts, to identify potential threats before they become an issue.
- User and Entity Behavior Analytics: The SOC should use analytics to understand user and entity behavior, identifying abnormal activity that may indicate a security breach.
- Continuous improvement: The next generation SOC must be committed to continuous improvement, regularly evaluating its performance, and making changes to improve its effectiveness.
In summary, the next generation SOC should be agile, automated, and integrated with other security technologies. It should leverage AI and ML to improve threat detection and have an integrated incident response plan. The SOC should be cloud-native and embrace DevSecOps practices, proactively search for threats, use analytics to understand user and entity behavior, and be committed to continuous improvement.
If you have queries related to 𝘾𝙮𝙗𝙚𝙧 𝙎𝙚𝙘𝙪𝙧𝙞𝙩𝙮, reach out to our in-house Cyber Security experts. They are happy to hear from you info@cmsitservices.com. You could also reach out to us on our website https://www.cmsitservices.com/contact-us/.




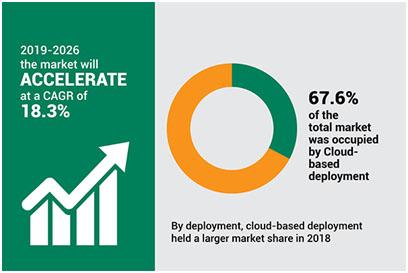 Cloud Costing Model: Awareness of the cloud costing model is a must. The number of products by a cloud services provider is daunting. As an example, AWS has 169 products whereas GCP has 90 products. Many costs are hidden in nature and many of them must be discovered on the way. Therefore, right experts are necessary to make sure the cloud costs are optimized to the best of the ability.
Cloud Costing Model: Awareness of the cloud costing model is a must. The number of products by a cloud services provider is daunting. As an example, AWS has 169 products whereas GCP has 90 products. Many costs are hidden in nature and many of them must be discovered on the way. Therefore, right experts are necessary to make sure the cloud costs are optimized to the best of the ability.